Looking for Physical Security Solutions can be overwhelming with the amount of choice offered these days. From solutions that promise to optimise your security, organise your documents, streamline administrative tasks, or improve your customer service. All of these outcomes are of course useful, but do you really need 10 separate solutions to get the best benefits?
Following the digital transformation is no longer just a good idea, it’s a matter of staying competitive in a landscape where a better work-life balance and a high standard of safety are necessary to attract and retain good workers.
In our previous blog, we already spoke about how physical security automation will help to improve the workplace experience, but taking this a step further, what are the key features you should look for in Security Solutions that improve all of these areas directly?
In this blog, we look at the benefits of having security solutions integrated with other systems, such as visitor management, and the top features to look for that will improve workplace security and experience.
- Understanding security solutions
- What are the benefits of integrated security solutions?
- Key features to look for in integrated security solutions
- How do you choose a system that works best for your organisation?
- Final thoughts

Understanding security solutions
A physical security solution encompasses a range of strategies and technological tools designed to protect assets, individuals, and premises against unauthorised entry, theft, harm, or damage. These comprehensive solutions are strategically implemented to fortify the safety and protection of tangible environments, including but not limited to buildings, facilities, data centres, and vital infrastructure.
A study by Kensington revealed that the second most common place for theft to occur (with 23%) is actually in the office, which is another reason why it is so important to keep track of everything that happens at your facilities.
Visitor management systems are one of the most used security solutions and one of the most vital. Visitor management is the process that helps your organisation keep track of the people who enter your facilities – visitors, contractors, employees, and everyone in between. It is an extension of your security team, meant to operate alongside them to enhance building security and facilitate the best possible FOH management.
Alongside other security systems, such as access control, CCTV, and AI-driven data insights, a VMS is a powerful tool in your security automation toolbox – especially when you utilise system interoperability in your tech ecosystem.
How much data do you collect, perhaps even unknowingly, without the tools or knowledge to turn it into actionable insights? A lot of companies struggle to get a grip on their data despite the challenges they face, and numerous organisations lack a coherent overview of everything due to the data dispersion across siloed systems and various locations.
Security automation with integrated solutions can rectify this issue by aggregating data from pertinent systems and streamlining it into a cohesive format. This consolidated data can then be effectively analysed to extract valuable and practical insights.
What are the benefits of Integrated Security Solutions?
Benefits of implementing an integrated security solution with your VMS include:
- Eliminating false security alarms
- Creating a much more attractive workplace
- Reducing manual labour and repetitive tasks
- Saving time and costs from improved efficiency
- Making a great first impression every time
- A centralised platform for monitoring data
- Reducing queues at reception
- Making it easy and intuitive for everyone to navigate the facilities
- Improving response times in case of emergencies
- Having a dedicated support team in case any issues arise with your system
- Staying up to date with automatic updates
- Monitoring and optimising a well of service devices automatically
- Always staying compliant by monitoring data against service level assurances in real-time
- Creating an engaged workplace
Key features to look for in integrated security solutions
The right security solutions streamline processes to strengthen security measures and significantly reduce the chance of errors occurring. If you are looking for a solution that can elevate both security and experience, there are a few key things you should look for. These are features that make work easier for your employees, processes faster for visitors, security more robust, and the workplace much safer.
Here are 8 features for choosing the best-integrated security solution:
1. Streamlined visitor registration processes
It’s important to know exactly who comes and goes from your locations, and it’s equally important to ensure that they have their legal documents, NDAs, and practical information in place. All of this data is usually captured upon arrival for visitor registration, which can take up a lot of time at reception. Look for a system that allows for a streamlined check-in process with maximum security measures. This is doable by enabling a pre-registration process through a visitor management system.
Before arriving on-site, visitors, contractors, and other types of guests receive an invitation containing a link to pre-registration, where they can key in their details sign any important NDAs and answer questionnaires. This saves time for both staff and visitors without compromising on security.
2. Access Control Integration
Implement watchlists from your local area or on a national level and create your own blocklists where you can add people who are banned from your locations. The system will thus automatically reject unwanted visitors when they scan their IDs and notify staff so the appropriate measures can be taken.
Look for the ability to integrate with your access control systems for a synchronised approach to security. Physical security solutions can automatically grant or restrict access to specific areas based on visitor credentials. For instance, a visitor’s badge can act as a key card to access authorised areas.
3. Cloud-based Security & Data Privacy Compliance
With stringent data privacy regulations in place, how the security solutions store and manage data should be part of the key considerations, ensuring compliance with standards like GDPR or HIPAA.
Look for features like data encryption, cloud-based storage, ISO27001 accreditation, and automatic data retention period setting – ensure that your data is backed up regularly so it’s always available in case of an incident. Rather than having private information or important documents physically, storing it this way in the cloud helps avoid the risk of it being misplaced, exposed, or stolen.
4. Instant alerts and notifications
Seek out features that provide an automated cross-reference of visitor data against watchlists, triggering real-time alerts upon a visitor’s arrival. This helps employees or security personnel to identify potential security threats or individuals with restricted access.
Security monitoring systems can automatically alert staff of any incidents or irregularities with information collected from CCTV, occupancy sensors, and visitor management systems. Additionally, a check-in system can notify hosts when their visitors arrive, ensuring clear communication for visitors to be picked up – and if the host isn’t present, a workflow can be set up to notify the next available employee.
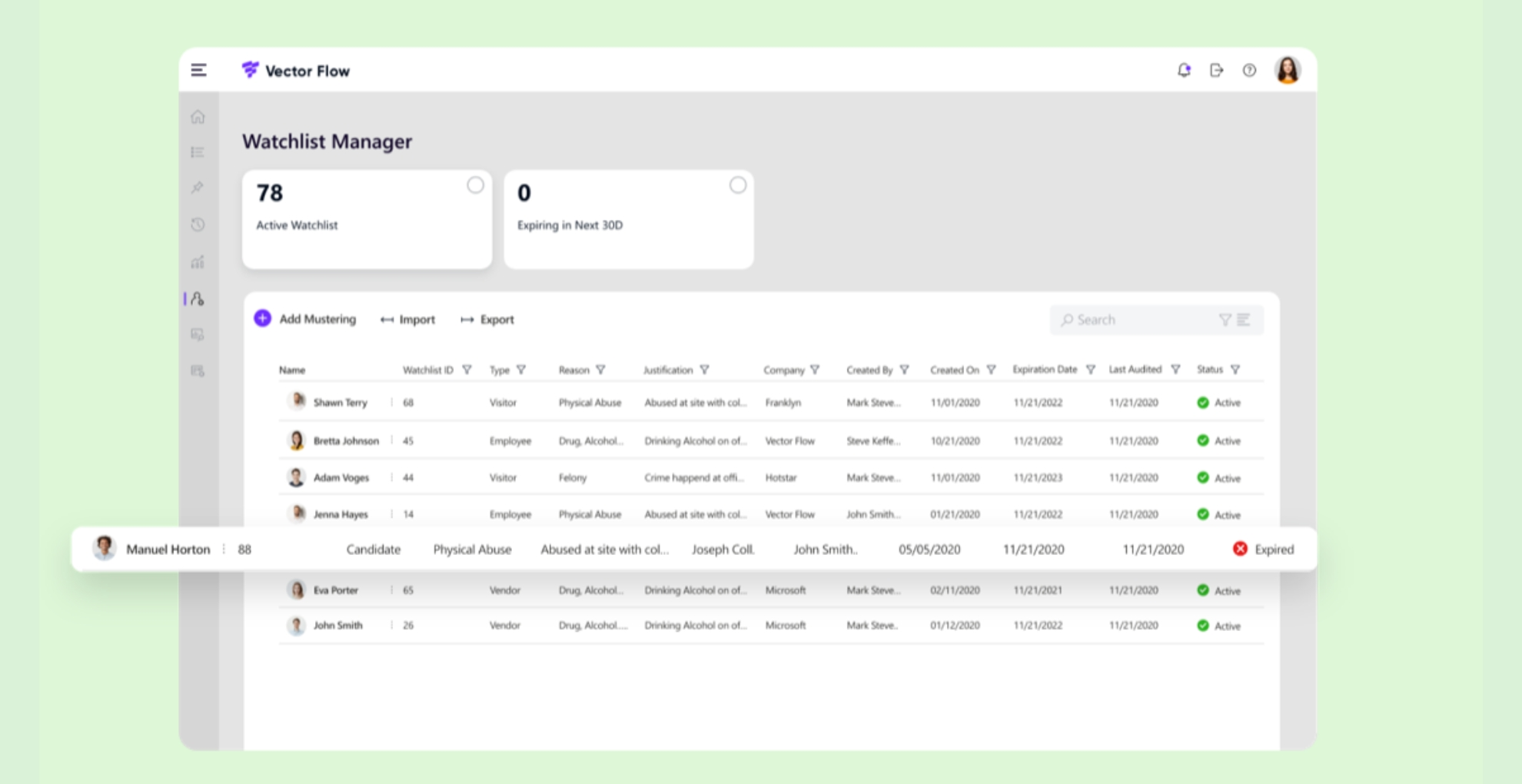
Visitor watchlist
5. Integration and scalability
Security automation and tech is an ever-evolving field, so it’s important to ensure that the solutions you implement can last for a long time. The compatibility with existing security infrastructure is crucial for simplifying processes and expanding the systems’ functionalities.
The best systems provide scalability so you can continue to grow your business and add more locations while maintaining a centralised overview.
6. Visitor tracking
Your physical security solution should create comprehensive visitor logs and histories, making it easy to access past records for auditing purposes or incident investigations. The security system can track people in the facility, providing real-time data on each person’s location and the duration of their visit, and the historical data can be invaluable in identifying patterns or trends in visitor behaviour.
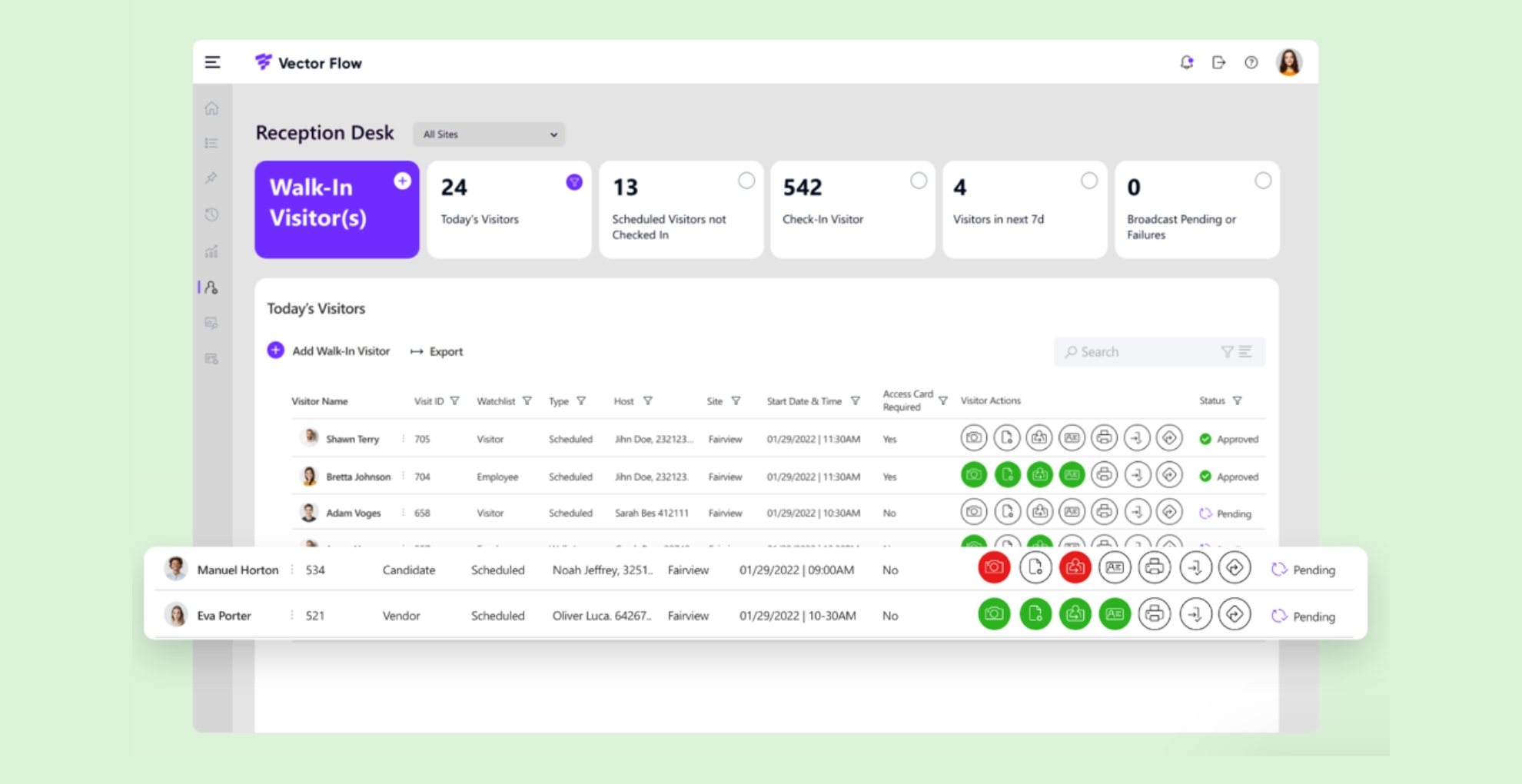
Real-time visitor tracking of their check in/out time, and their activities at your facilities.
7. Check-out access revoking
It is useful to have a system that will automatically revoke access credentials when people check out, ensuring that a one-time visitor can’t enter again later without permission. Additionally, access permissions can be set up to expire at certain times, meaning access is revoked automatically at the right time.
8. AI-driven data insights
Manually analysing the tremendous volume of data that today’s physical security systems generate is a significant challenge for security teams to manually analyse; however, ignoring the data reduces your chances of staying ahead and your ability to continuously improve. This is why AI-driven security solutions like Vector Flow’s PIAM prove valuable. These solutions leverage artificial intelligence to process and interpret large datasets to get valuable insights that can be shared with the security team, helping you stay informed of emerging threats and trends
How do you choose a system that works best for your organisation?
These points are good as a general idea of what useful features to look for, but how do you know if a solution will be right for what you need? Many organisations look to workplace consultancy to support their tech purchasing decisions, but that might not be first on the list for everyone.
If you want to gather your own overview first, here are our suggestions for what to consider when making your choice:
Choose the right hardware
Although a lot of security solutions are software, you should consider whether a dedicated type of visitor management hardware would benefit you – especially for your reception area. You need a physical set-up that suits your building, branding and company culture to ensure that the system works to its fullest potential. Consider whether you need a tablet check-in system, a desktop, or perhaps a fully customisable reception kiosk.
The Vgreet software can be run on all these types of hardware, but for the fullest customisability and complete personalisation, the Vgreet kiosk is ideal.

Vgreet virtual reception kiosk at Sodexo HQ in London.
Consider the tangible and intangible ROI together
The purpose of security automation is to streamline processes and enhance productivity, but you shouldn’t implement a new solution just for the sake of it.
We have previously talked about how to measure the ROI of visitor management software. If you want to get an idea of what ROI might look like with an integrated system between VMS and SOC automation, you can check out Vpod’s ROI calculator here and Vector Flow’s ROI calculator here.
Identify your own challenges
What areas do you need the system to improve, and how comprehensive do you need it to be? If your office consists of two meeting rooms, a kitchen and a common room, maybe you don’t need a complicated system for access control; whereas, if your organisation spans several buildings across different countries, this would be essential.
Understanding your own challenges and how best to tackle them is essential to creating sustainable improvements. If this is something you struggle with, you might benefit from a workplace consultancy service, with experts who can help you interpret your data and understand your company culture. If this is something you would be interested in, you can read more about Vpod’s Workplace Consultancy here.
How easy is the transition?
It’s important to consider what the onboarding process will look like – especially if you are moving from a legacy system to modern software solutions. It’s important to choose a vendor who can provide proper support with implementation and integration. It doesn’t matter how top-notch a solution is if you don’t teach your workplace to use it properly.
With Vpod Smart Solutions, our experts are with you throughout the whole process and beyond. Our team becomes your team and our partnership with Vector Flow means that the integration between the systems is done seamlessly.
Final thoughts
Too often, companies and organisations will have no clear idea of the inner workings of their own workplace – what processes work and which don’t – simply because they aren’t monitoring the most meaningful data. As Bruce Barcley explains in his award-winning article from 2019: “The workplace is an ecosystem, an integrated system of interactive parts that require a holistic understanding and strategic approach”, so having siloed systems really isn’t beneficial.
An integrated security solution alongside a powerful visitor management system can help automate those security processes and shed light on which insights are actionable.
The partnership between Vpod Smart Solutions and Vector Flow offers a well-rounded and fully integrated solution. Vector Flow’s AI-driven solutions take security to a whole new level without creating an extra workload for your security team. With Vpod’s visitor management kiosk, you can provide a fully customised visitor experience, even before visitors step through your doors – a great first impression every time.
Read the press release for the partnership here and contact us to hear how we can help improve security and enhance the experience at your workplace!
Read more:


