Are you considering information security while purchasing a new cloud-based solution, such as visitor management systems and smart lockers? A data breach can lead to financial loss, damage to reputation, legal disputes, and loss of trust from customers and clients. If you are looking to learn more about this topic, we will talk about Vpod’s approach to information security concerning visitor management and smart locker technology, dissect the potential risks they pose, and delve into the strategies and best practices that can be employed to safeguard sensitive information.

What is Information Security and what does it mean in the modern digital world?
Information security (sometimes called InfoSec) is a set of best practices for safeguarding your digital information throughout its lifecycle in your systems. Just as you would want to protect your physical belongings, your digital assets also need to be “locked away” and protected from potential cyber security risks. This includes preventing unauthorised access, corruption, or theft of any data.
The concept relates to general data security, ranging from the physical protection of hardware and storage devices to the implementation of administrative and access controls. Lastly, digital data security also encompasses the logical security of software applications and extends to organisational policies and procedures.
Furthermore, with the rise of remote work and cloud-based solutions, it has become even more important to prioritise Information Security. As organisations embrace digital transformation and rely on interconnected networks, the potential risks and consequences of a security breach are higher than ever before.
Why is information security crucial while considering a technology solution?
Information Security is a crucial aspect to consider as they handle sensitive data, such as customer information, financial records, and proprietary company data. A security breach can result in severe damages: financial loss (the average cost of a data breach was $3.86mio in 2020), damage to reputation, legal liabilities, and exposure of sensitive or confidential information.
Various data privacy laws and regulations set standards for organisations to comply with in order to protect personal information. Examples include the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States.
While these basic standards do exist, such as local, national, or international laws and regulations, industry best practices, and technical accreditations, that does not mean that every tech solution provider meets the security standard. This is why we want to shed light on Vpod’s approach.
Vpod Smart Solutions Information Security Protocol
As a technology solution provider, at the core of our innovation is an unwavering commitment to safeguarding your data. We go beyond mere compliance with regulations and industry standards; we actively collaborate with security solution partners who share our vision for uncompromising data security.
SafeContractor & ISO27001 Accreditation
Vpod Smart Solutions is SafeContractor approved ISO27001:2022 certified to provide the highest security standards in ethical, physical, and digital contexts.
Cloud-based software and secure servers
Vpod Smart Solutions work with cloud-based software that provides somatic and regular security patches to prevent systems or processes from becoming outdated and therefore vulnerable to attacks.
Studies have shown that around 90% of websites are vulnerable to attacks, and 95% of these vulnerabilities could result in information being leaked due to outdated software. This underlines why it’s so important to keep your system up-to-date with the latest security patches. Especially for legacy systems that may become outdated or where you are at risk of falling behind on updates.
What are the Information Security features of Vgreet virtual reception kiosk?
Visitor Management Systems often store sensitive information such as visitor names, contact details, photos, purpose of visit, and identification documents. Proper security measures are essential to safeguard this data from unauthorised access – which includes keeping the software safe from both external and internal threats.
Our Vgreet virtual reception kiosk can integrate with various software systems to create the most comprehensive and customisable reception solution. For this reason, our summary here will focus on how information security is handled on our basic VMS software:
Regular software updates and security patches
The system is automatically updated to fix any issues that have been reported by clients, ethical hackers, or found through vulnerability scanning.
Data encryption
Encryption is pivotal in information security, converting plain text into unreadable ciphertext using complex algorithms, accessible only with the decryption key. All communications are encrypted using HTTPS and Transport Layer Security (TLS). All server hard disks are encrypted along with the databases stored on clients’ hardware. Finally, passwords are never stored in formats readable to humans.
UPS and backup generators
Sudden power outages or fluctuations can lead to data corruption or loss. UPS (Uninterruptible Power Supply) systems and backup generators provide continuous and reliable power to data centres. Furthermore, Vgreet’s standard software has a publicly available webpage for clients to check system status and incident reports.
Access rights and control
Vgreet has granular access control with various permission levels that clients can set up, e.g., admin, reception, security, assistants etc. Similarly, all access for software developers is restricted on a need-to-know basis and utilises multi-factor authentication.
Protection
All files and attachments uploaded to the system are automatically checked for malicious content. Alongside redundant firewalls, audits, and Intrusion Detection Systems (IDS), this protects from cyber-attacks.
Personal data privacy
The Vgreet system uses logical segmentation of data on a code level, maintains comprehensive audit trails, and automatically deletes visits after a designated retention period. The system tracks changes made to visits, when the changes were made, and by whom. This allows you to stay compliant with privacy regulations like GDPR.
For more information related to data security, click here.
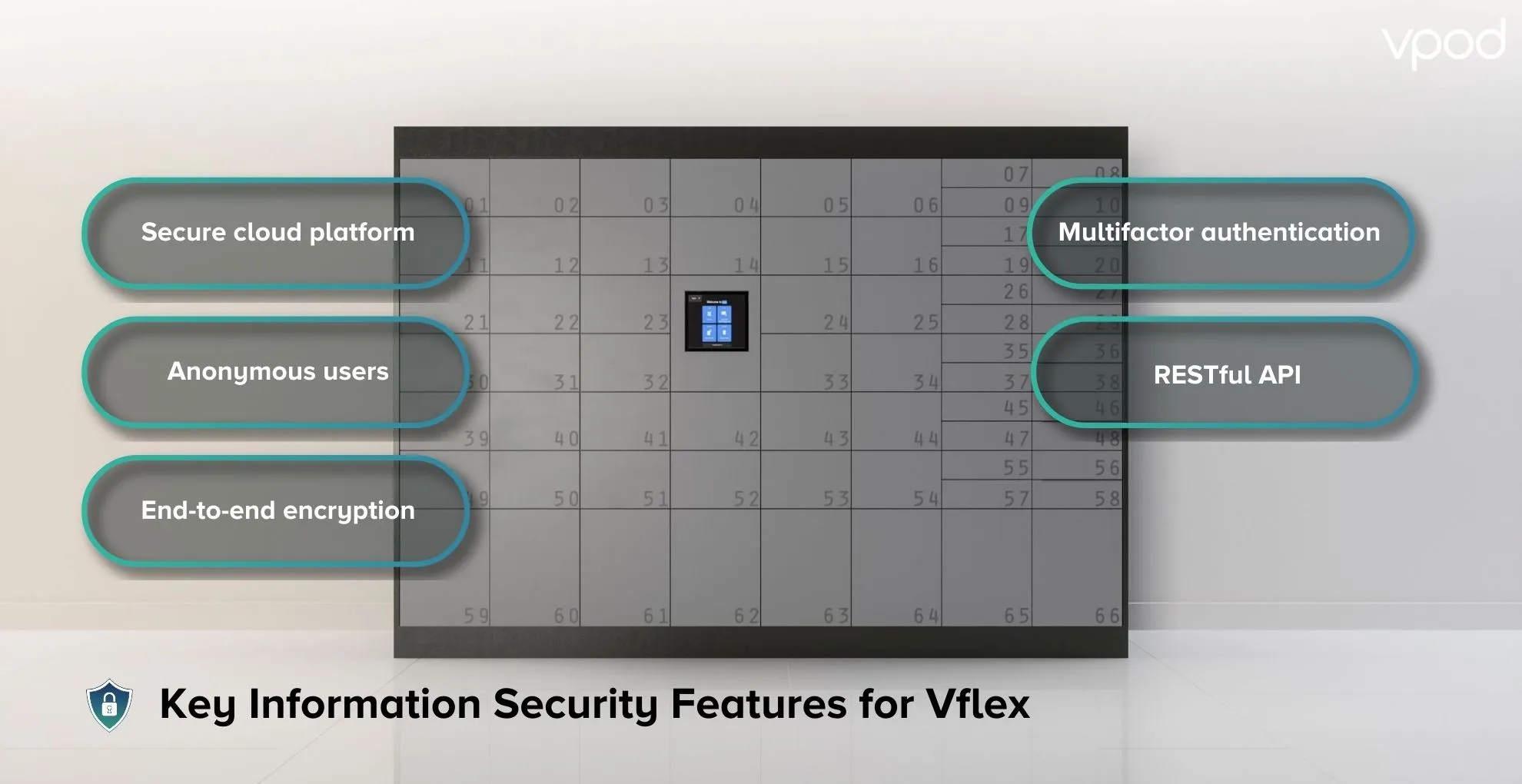
What are the information security features of Vflex Smart Lockers?
Smart locker systems typically require some access to personal data for users, which might include details such as name, employee ID, email address, phone number, photo, and biometric data. Additionally, if the system collects records of the access history of each user, this also requires attention to ensure compliance with information security regulations.
Here are the main points of how Vflex handles information security:
Secure cloud platform
The Vflex system receives regular updates to fix any bugs or reported issues and ensures high standards of quality with ISO9001 and security with ISO27001 certification. The locker management software is in the cloud, via the well-secured (Azure) platform, and the servers are located in data centres with strict rules for both physical and digital security.
Anonymous users
The system offers several authentication methods for individual users and only stores the data you give it access to, but if you don’t want any data sitting on an external point, it is possible to have fully anonymous users.
Firstly, the touchpad on the locker wall itself allows users to generate temporary 4-digit PIN codes that can be used during a set time period without having to provide any personal details.
For more functionalities, users can use their already public company email. Employees, visitors, and clients alike can receive a 6-digit PIN code through the provided email that they can use to access lockers at any time. This way, the locker system itself has no personal details stored; however, security can still track occupancy and users based on the emails.
The locker app can also be used anonymously: users receive a unique password through their email that they can use to log into the app. Through here, they can book, access, and lock their lockers easily, still without needing to disclose any personal data.
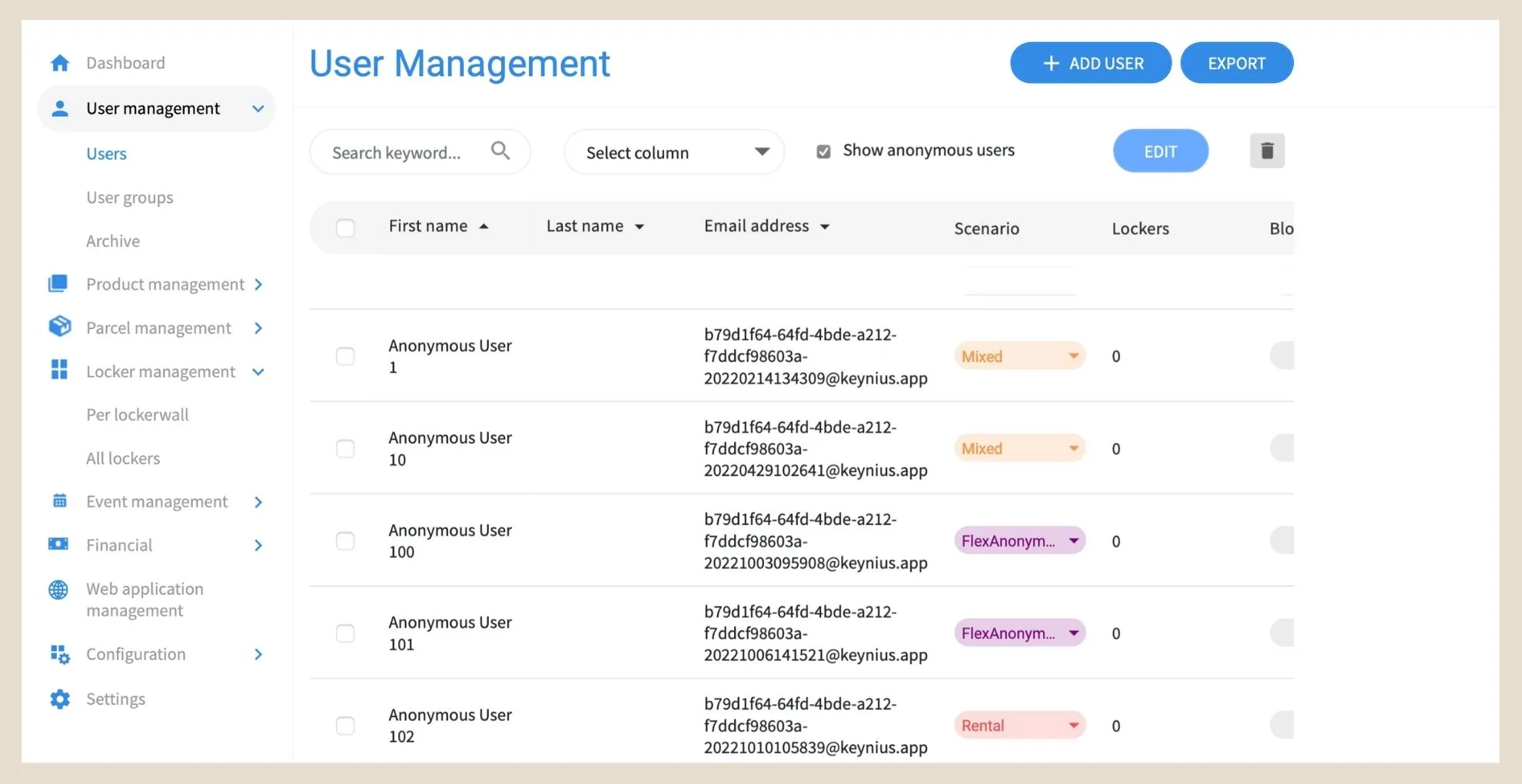
No personal information is collected from the smart lockers.
End-to-end encryption
All data communication with users is encrypted and unreadable for unauthorised persons. Vflex employs 128-bit AES encryption protocols or higher to secure the communication between the lock and the controlling device.
Multifactor authentication
Vflex can configure multi-factor authentication, providing an additional layer of security to guard against unauthorised access.
In case of a power outage
The lockers use mechanical override that managers can access with a key at the bottom of the locker bank. In case of a sudden power outage, the lockers will not open spontaneously, but will instead stay locked. Unlike a UPS that gives you only about an hour of time to get everything sorted, a mechanical override functions completely without electricity. To open lockers, the mechanical override can be pulled to access the lockers.
RESTful API
The Vflex platform uses RESTful APIs to communicate and exchange information securely with other systems through integrations. This means that the locker system does not share any unnecessary data with other software and does not take any data it does not need in return. Additionally, all systems can be updated and changed without affecting the integration or causing vulnerabilities.
How to maintain a high standard for information security![]()
Stay 2 steps ahead
The most important thing to remember for information security is that things are always changing. The moment a new security measure is implemented, there will most likely be someone out there ready to try and break it. This is why it’s so vital to look for solutions that use things such as bug bounty hunters, penetration testing, and an updated vulnerability disclosure policy.
Additionally, it cannot be stated enough how important it is to keep your systems updated. For office security, it is generally not recommended to use legacy systems as they require manual updates, but if you do decide to keep your legacy system, always keep it updated!
Collaborate with trusted vendors
Working with trusted vendors means, beyond just researching the solution and software itself, you need to know how the vendor conducts their business and if they, along with their system, are certified to handle your data.
At Vpod, not only do our products uphold the highest standard of digital security, but we also got our ISO2700 accreditation updated to the latest 2022 version. We want to ensure full trust and security, which is why we’ve ensured that both our products and internal processes are completely compliant.
Implement security into your organisational culture
Security awareness training educates employees about the various threats they may encounter and the best practices to mitigate these risks. This includes creating strong passwords, awareness of confidential information, and implementing efficient and secure processes for handling data. By fostering a culture of security awareness, organisations can significantly reduce the likelihood of security incidents caused by human error or negligence.
Continuous monitoring and incident response plan
Having an incident response plan is crucial to effectively handle security incidents. This plan outlines the steps to be taken in the event of a security breach, ensuring that the incident is addressed promptly and minimising its impact.
Summary
In conclusion, information security is crucial in protecting sensitive data and ensuring the viability of tech solutions. As technology continues to evolve, the significance of information security becomes even more evident. By prioritising information security, organisations can effectively mitigate risks, safeguard data, and build trust in an increasingly interconnected and vulnerable digital landscape.
As a company, Vpod strives to provide the best possible service, which includes upholding industry best practices and standards of both digital and physical security.
If you have any more questions about our processes or our products, you are more than welcome to swing by our showroom for a chat or contact us here.
Further reading
- Navigating the Tech Landscape: Choosing the Ideal Security Solution
- How Physical Security Automation Will Promote Workplace Experience
- Technology and People: The Key to Unlocking Better Office Security